GISA saved 20 hours each day by automating vulnerability monitoring with Feedly Threat Intelligence
GISA, a German MSSP, saves money, time, and team brain power by automating the process of collecting, analyzing, and sharing vulnerabilities.
Since we started using Feedly, we often have a head start of up to three days before information is communicated by authorities."
OVERVIEWThe short version
The customer: GISA is a leading IT service provider in Germany. They offer comprehensive services, including strategy, consulting, development, and implementation of business procedures and IT infrastructure. The security operations team is made up of 40-45 team members, and serves over 800 clients across Germany.
The challenge: Manual intelligence gathering and vulnerability monitoring was not viable with limited team resources. Each team member was spending up to three hours per day just to collect the intelligence required to do their job. It was costing them precious time, money, and brain power.
The solution: Outsource vulnerability monitoring to Feedly AI. The team set up AI Feeds to monitor their clients' tech stacks. Vulnerabilities are automatically sent to a ticketing system, freeing up everyone’s time.
The results: 50% less time spent collecting information. Not only did GISA’s security operations team save 20 hours daily of the team’s time, but they sped up the process of intelligence gathering by three days.
Start a trial of Feedly Threat Intelligence or keep reading to learn how GISA automates the vulnerability monitoring process.
THE CHALLENGEChecking 70 different websites a day is “time expensive”
To track vulnerabilities, GISA’s cyber threat intelligence (CTI) team had to check up to 70 websites multiple times each day. The CTI team spent up to 50 minutes during each of their three intelligence-gathering sessions — in the morning, at lunchtime, and in the afternoon —just to prepare intelligence to share with colleagues.
The analysts are trained specialists at finding this type of information, but it was still time-consuming and annoying for them to filter through duplicate information.
It’s also complex and tiring work. And as any hiring manager for CTI teams knows, there’s no surplus of skilled cybersecurity analysts waiting to fill empty spots. Michael Netzband, Director of Information Security, leads the security operations team and says, “I had to make the work happier and less tedious, because it’s hard to find security specialists. We had to find a way to use more automatic tools.” As team lead, Michael sought to eliminate this form of work as much as possible and make work fulfilling for his team so he could retain and develop talent over the long term.
“We had to find a way to use more automatic tools”
THE SOLUTIONGISA used Feedly Threat Intelligence to set up a process that saved 20 hours per day across the team
When Michael discovered that Feedly Threat Intelligence could take care of the information collection and deduplication process, he immediately started crunching numbers to calculate potential ROI.
“I sat down and calculated how many minutes per employee I would save if I were using a tool with information collecting, deduplication, and highlighting. Doing all that manually costs at least $100 per day per analyst. And when you have 20 people doing this work, you can see how much money you can save if you have this information at one click and nobody has to search each site manually. It was an easy choice to use Feedly.”
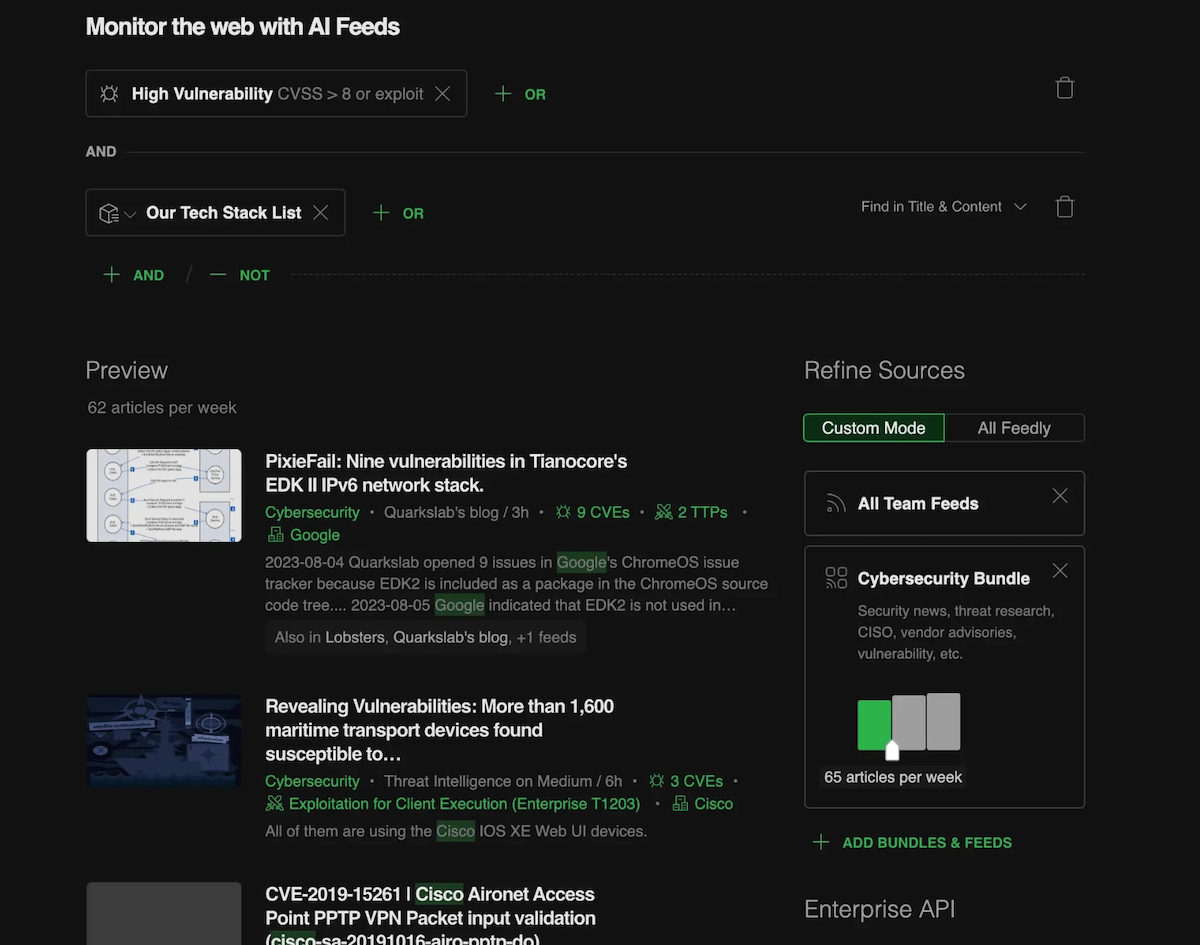
Outsourcing intelligence collection to AI Feeds
To outsource the tedious work of information collection, the CTI team set up AI Feeds to monitor the open web for:
- Vulnerabilities affecting GISA’s tech stack
- Vulnerabilities affecting the tech stacks of GISA’s clients
- CVEs with a CVSS score of greater than 8, or with a known exploit
Using Insights Cards to quickly get up to speed on CVEs and threat actors
After collecting intelligence, the team must analyze, distill, and organize the information.
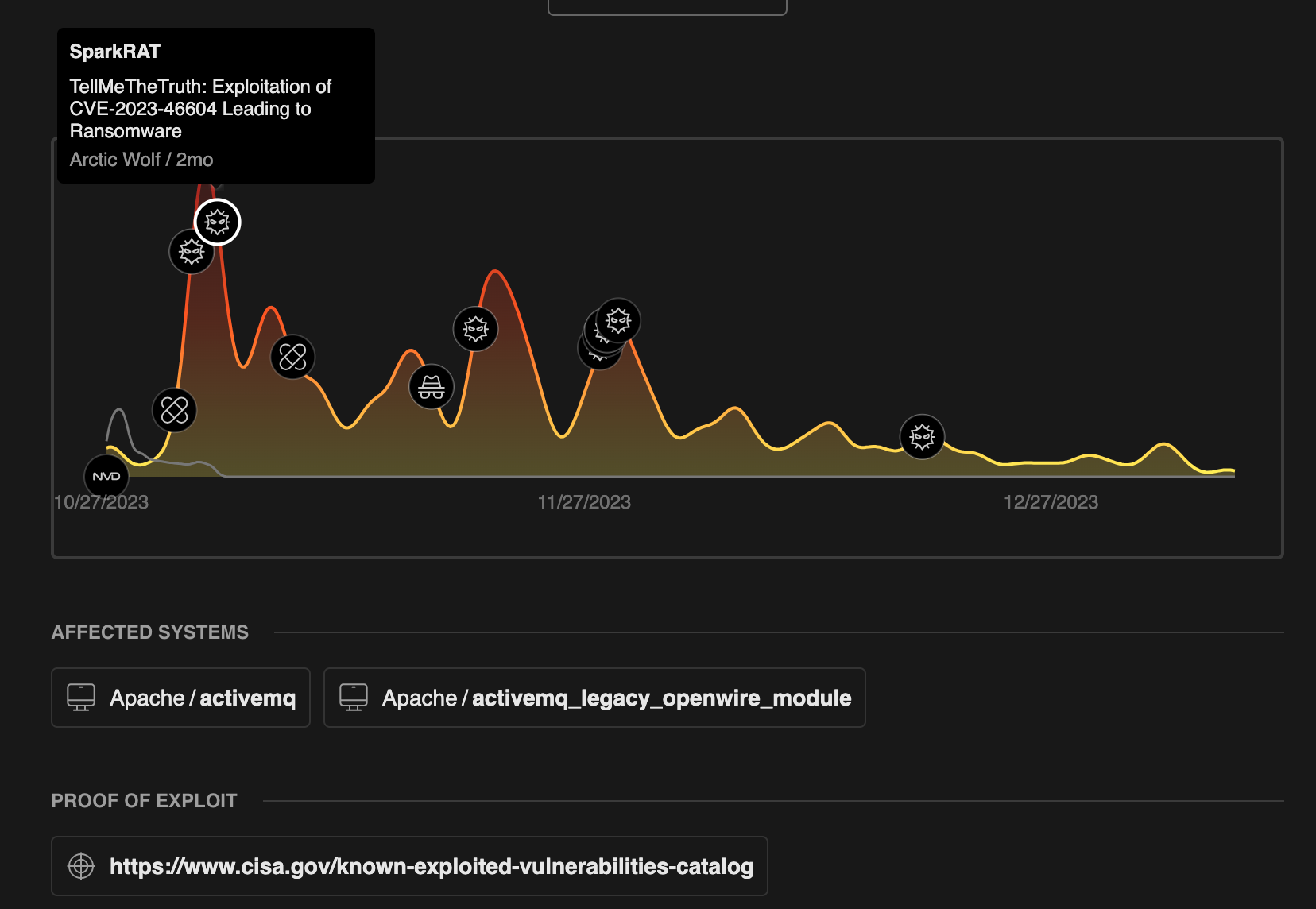
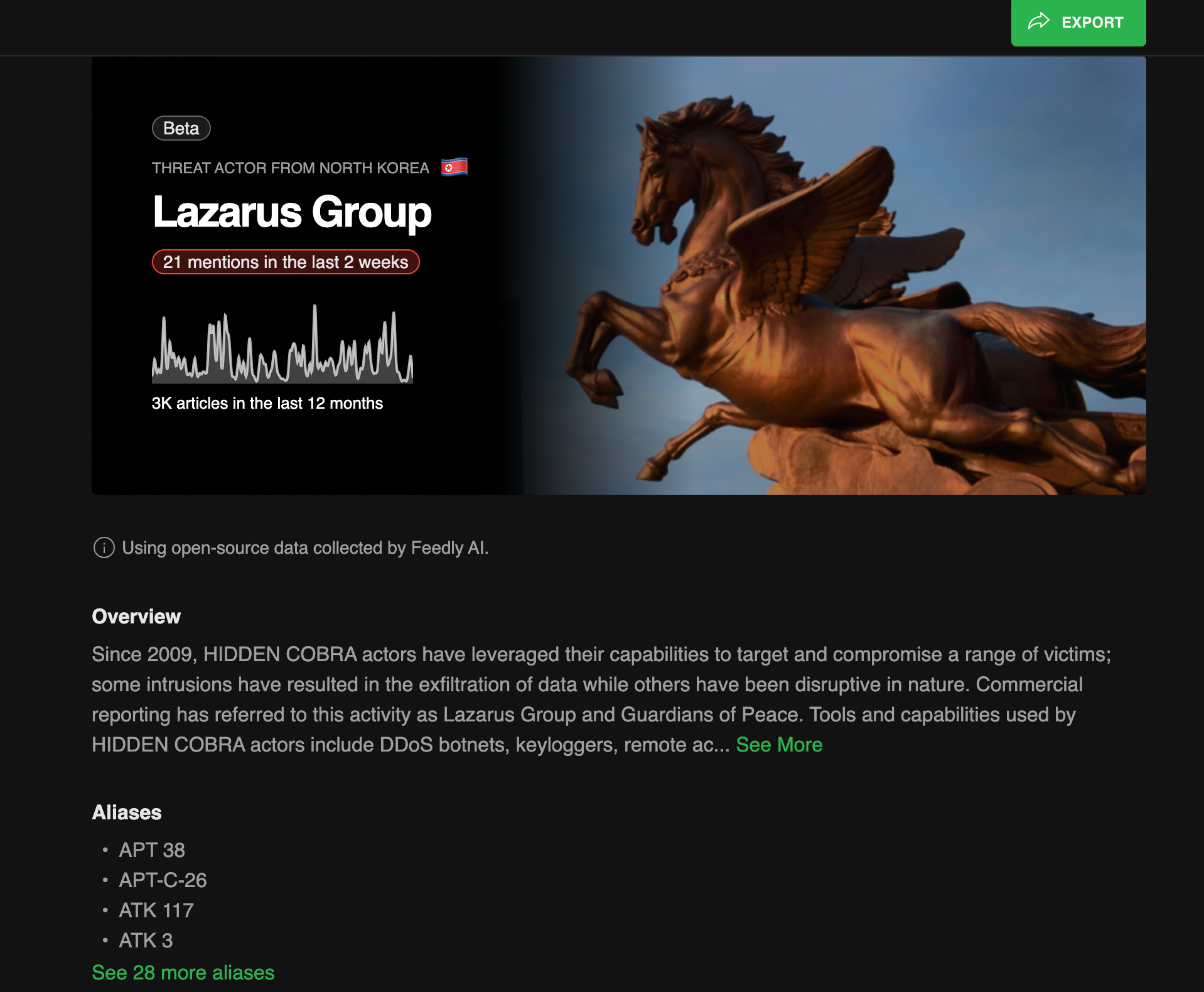
The CVE Insights Cards help analysts quickly get a picture of a CVE. “When we look at the CVE, the first thing we check is the trend graph. Then we check out the timeline to learn when it's first mentioned, when the exploit is out, when the patch comes out.”
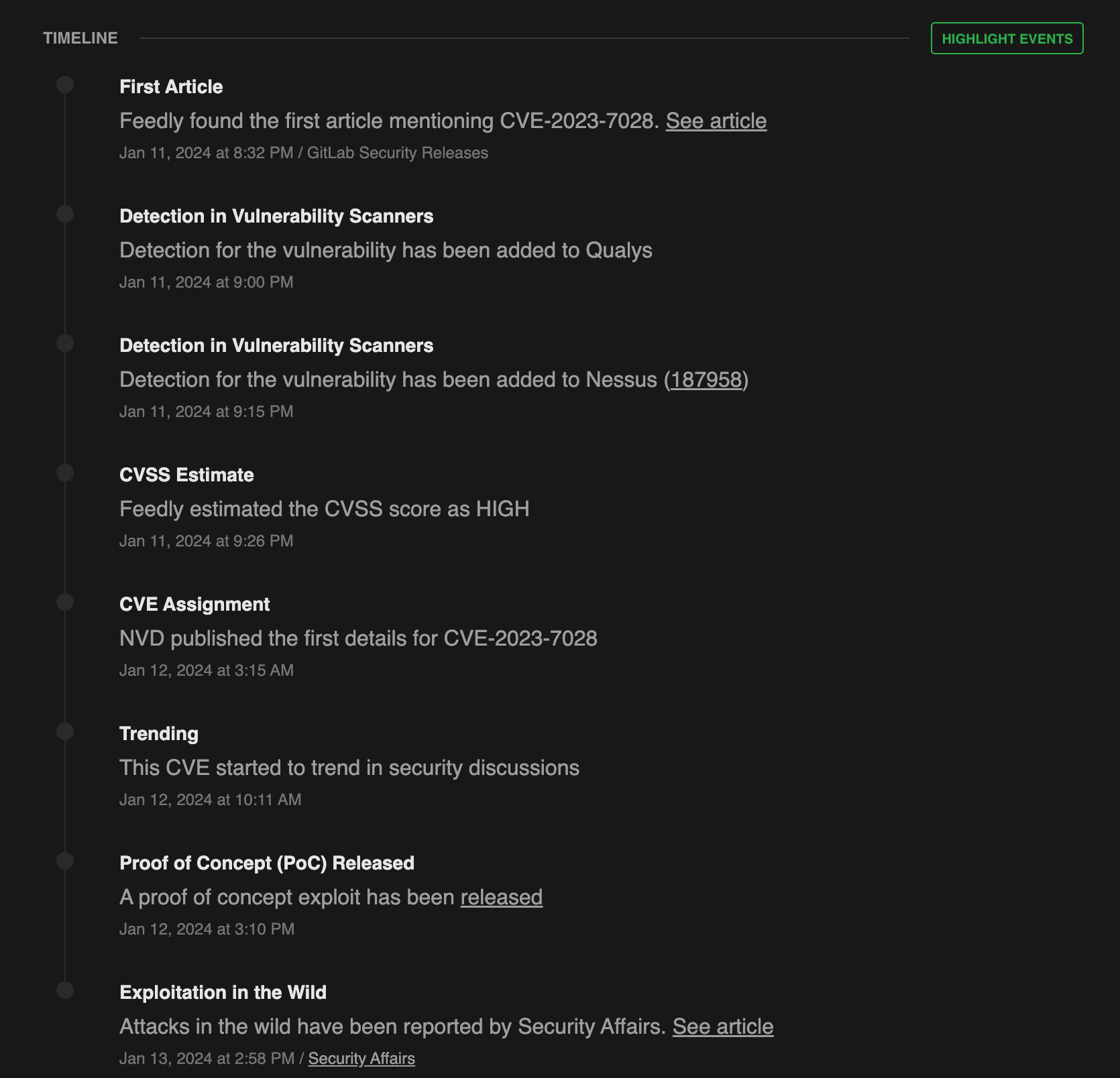
Analysts further drill down with Threat Actor Insights Cards, which both help educate newer analysts and clients of the context around a specific threat actor. With how difficult it is to find experienced, specialized security analysts in Germany, many have to learn on the job. The Threat Actor Insights Cards help give them the context as they’re working. “They have to learn by doing. And for newer analysts, this is especially helpful to have the attacker insights card, because they can get a 360-degree summary and dive deeper into the source articles.”
Automatically create vulnerability remediation tickets with the Feedly API
To further reduce the load of manual work on individual analysts, the security operations team has automated much of the process of transferring information from an article, opening a ticket, and getting it in front of the right analyst.
“When someone saves an article to our “transfer” Team Board, it automatically creates a ticket in our ticketing system. This pulls all this information from the article via the API.”
The ticket then gets sent to the first-line analyst, who then sends it to the team that needs the information most. That could be the networking team, the application team, or the Linux, Windows, or MacOS team.
Sending Automated Newsletters directly from Team Boards in Feedly
Apart from the automated ticketing system, the CTI team’s outputs include regular security reports for clients. GISA also sends Automated Newsletters directly from Feedly to a selection of clients weekly. The newsletter provides a general overview of the current threat landscape, and focuses on data breaches that may interest or impact their clients. Feedly populates each week’s newsletter issue from the CTI team’s Team Boards, and then AI generated summaries give an overview of each article.
THE IMPACTGetting information three days quicker than the national security news service
If I didn’t have Feedly anymore, I would need at least six to eight new employees, but it's not an option to not use Feedly.
Michael remembers relying on automated emails from authorities for information about security breaches, CVEs, and related intelligence in the past. He says, "Since we started using Feedly, we often have a head start of up to three days before information is communicated by authorities."
Freeing up the team by using Feedly AI to do the work of six to eight employees
The team now spends about half the time they used to spend collecting intelligence, saving about 20 hours per day. Michael adds, "So those 20 hours I’ve saved across the team daily, I can now use for other things.”
The CTI team serves 800+ clients, and now that so much of their time is freed up, they have time to go deeper with each incident. “The team spends more time researching the security information system, doing forensics, especially when new indicators of compromise come in,” comments Michael. “Before, they only had time to react. Now they can analyze, prepare, and respond more thoughtfully.”
Beyond time saved, using Feedly for open source intelligence collection has expanded the scope and capacity of what the team’s able to do. “If I didn’t have Feedly anymore, I would need at least six to eight new employees, but it's not an option to not use Feedly.”
Getting the right tools for the team helps prevent burnout and make the job more fun
CTI teams often face high turnover related to the pressure to do more with less. Michael is acutely aware of this challenge, and knows that utilizing automation (and tools like Feedly) can help automate the tedious parts of the job and make the overall experience more fulfilling.
“At every security operation center, there’s a big weight of burnouts, because there's more work than you can ever do. I want to prevent this on my team. So I try my best to get the right tools for my colleagues so they can work sustainably. Feedly takes over the complex and tiring part of finding information and lets the team focus on analysis and strategy instead.”
He adds, “Security engineers have to have fun at work. And I try my best to make it first, not an annoying job, and then a very interesting one.” We want to help security engineers have more fun at work too. And we’re so glad to help teams like GISA enjoy cyber threat intelligence more.
What could your team do if vulnerability monitoring were automated?
Start a free 30-day trial of Feedly for Threat Intelligence to start automating the process of vulnerability monitoring and outsourcing the tedious work.
Start Free Trial