Automatically collect and ingest open source IoCs
Includes rich context like threat actors, malware, vulnerabilities, and TTPs
No credit card required
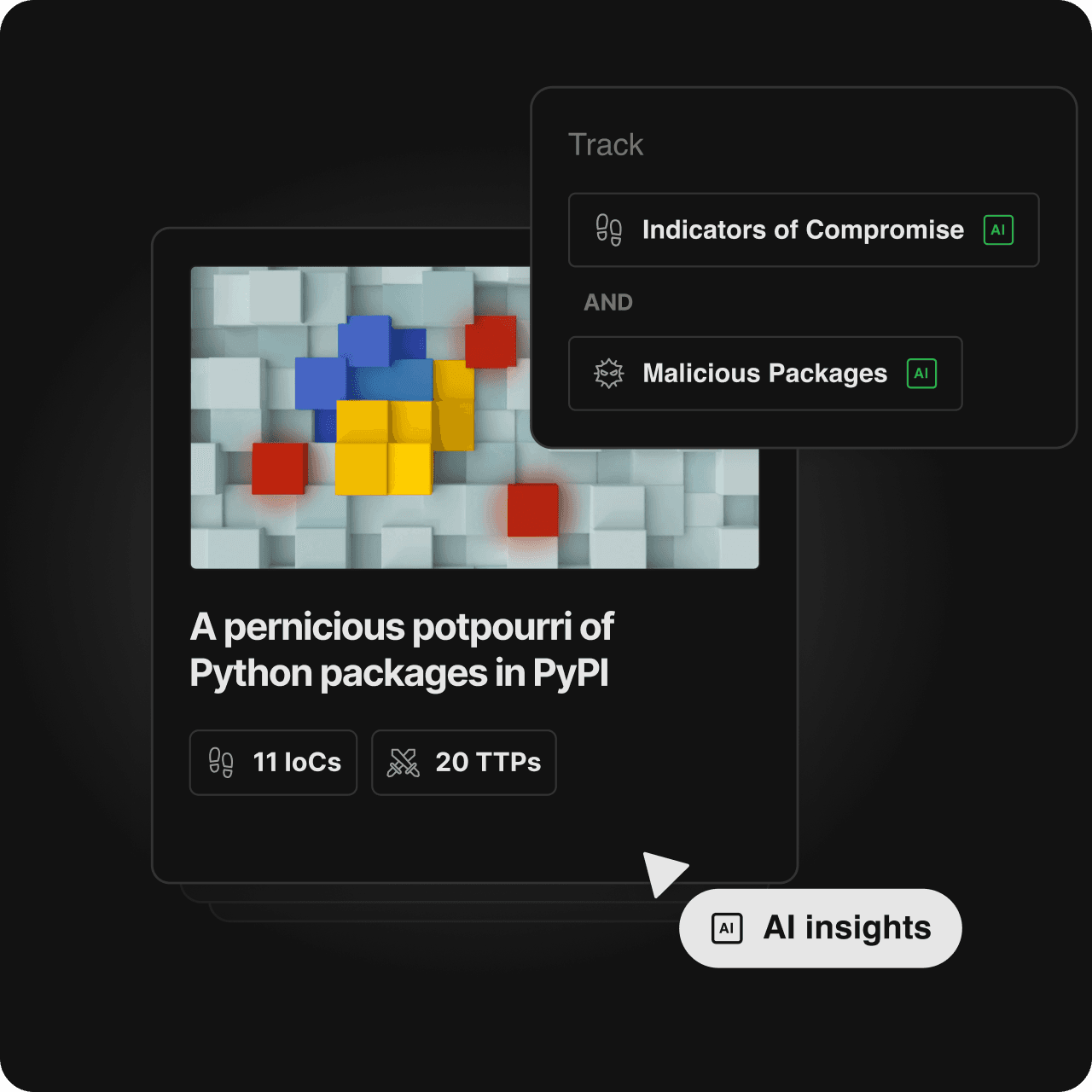
AI Feeds
Continuously collect open source IoCs
AI Feeds are AI-powered queries that collect relevant actionable insights from the open web
Customize to threat actors, malware, etc.
Scan intelligence reports, news, advisories
Filter out false positives
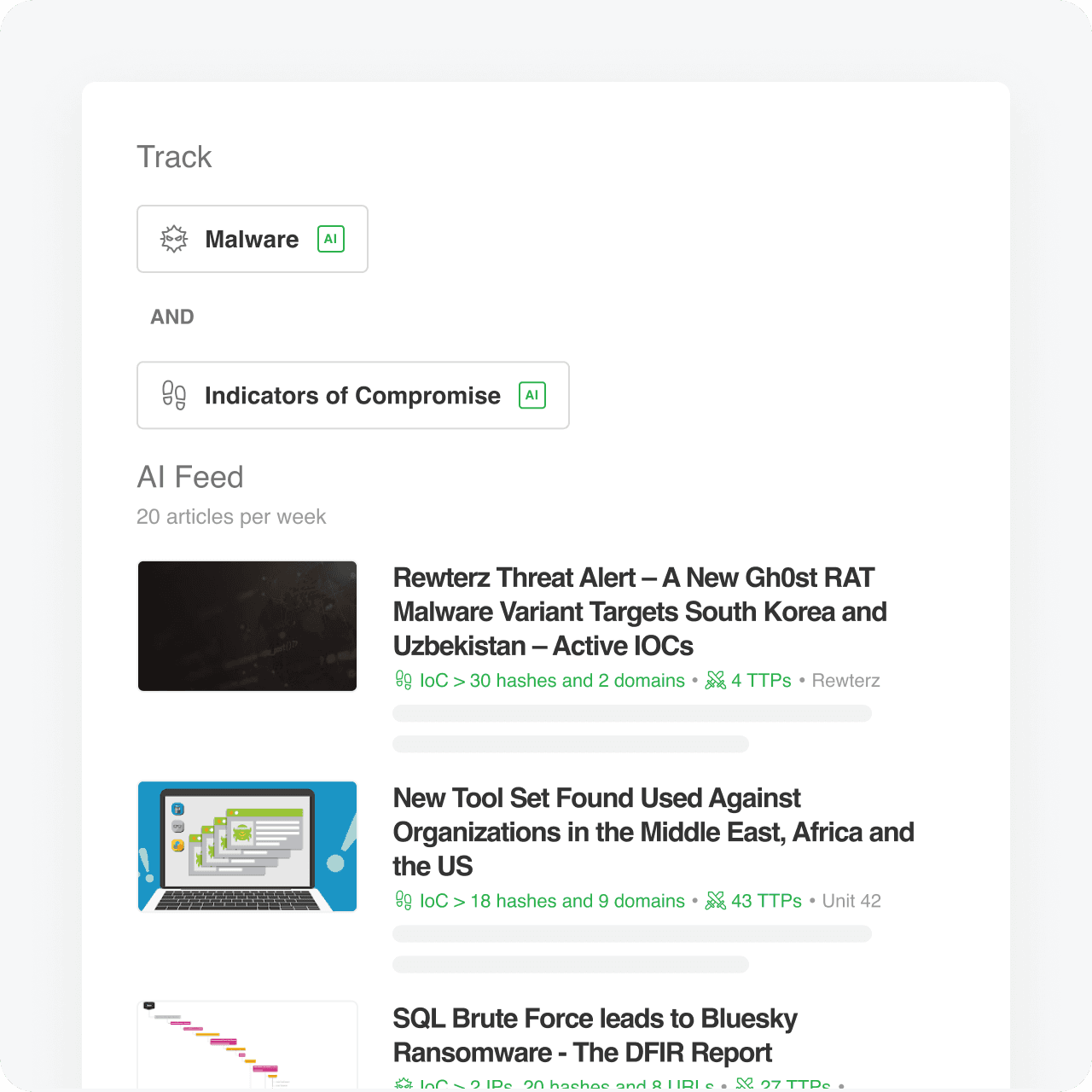
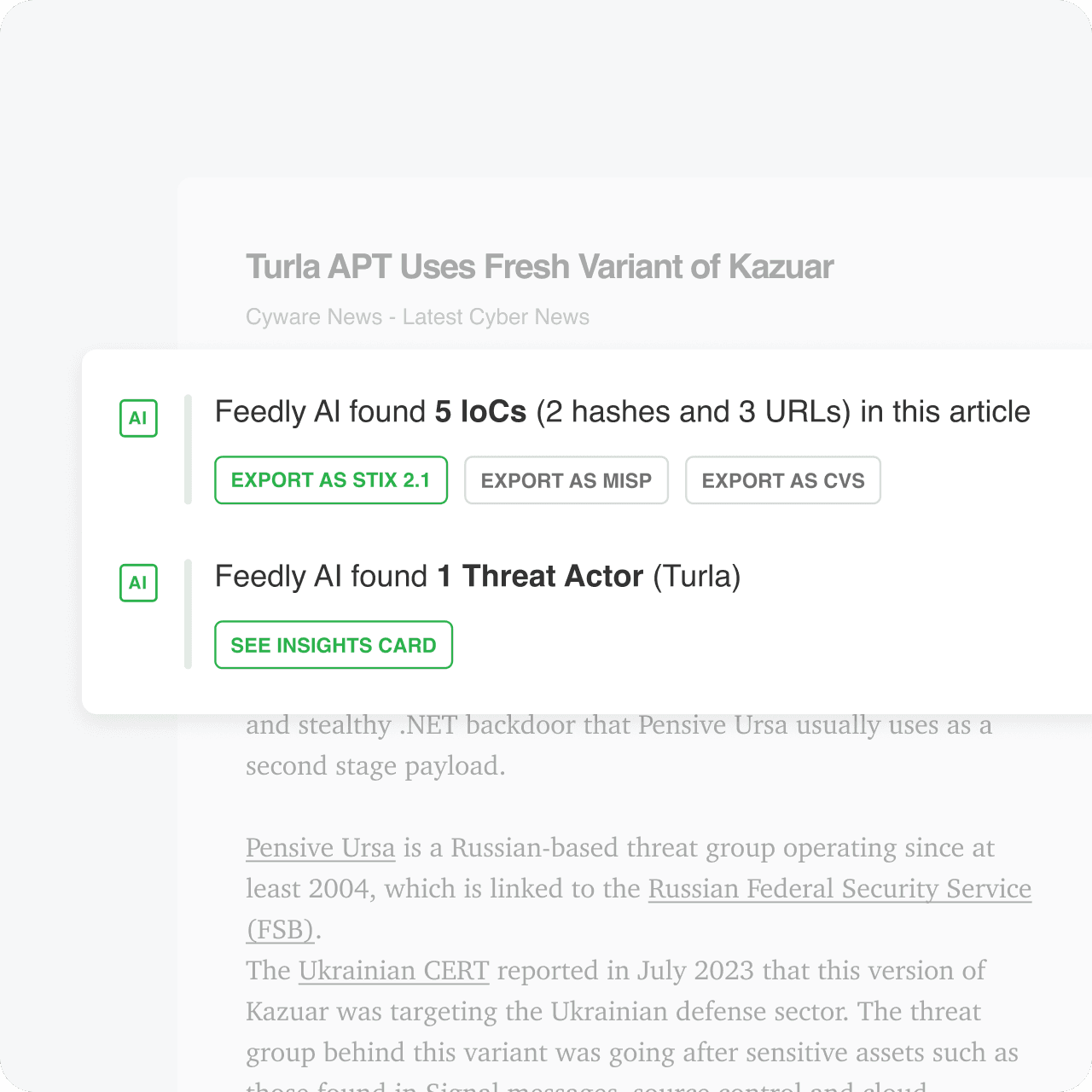
AI Insights
Automatically extract and enrich IoCs
Feedly AI automatically extracts, enriches, and links IoCs, TTPs, threat actors, malware, CVEs, etc., in machine readable formats
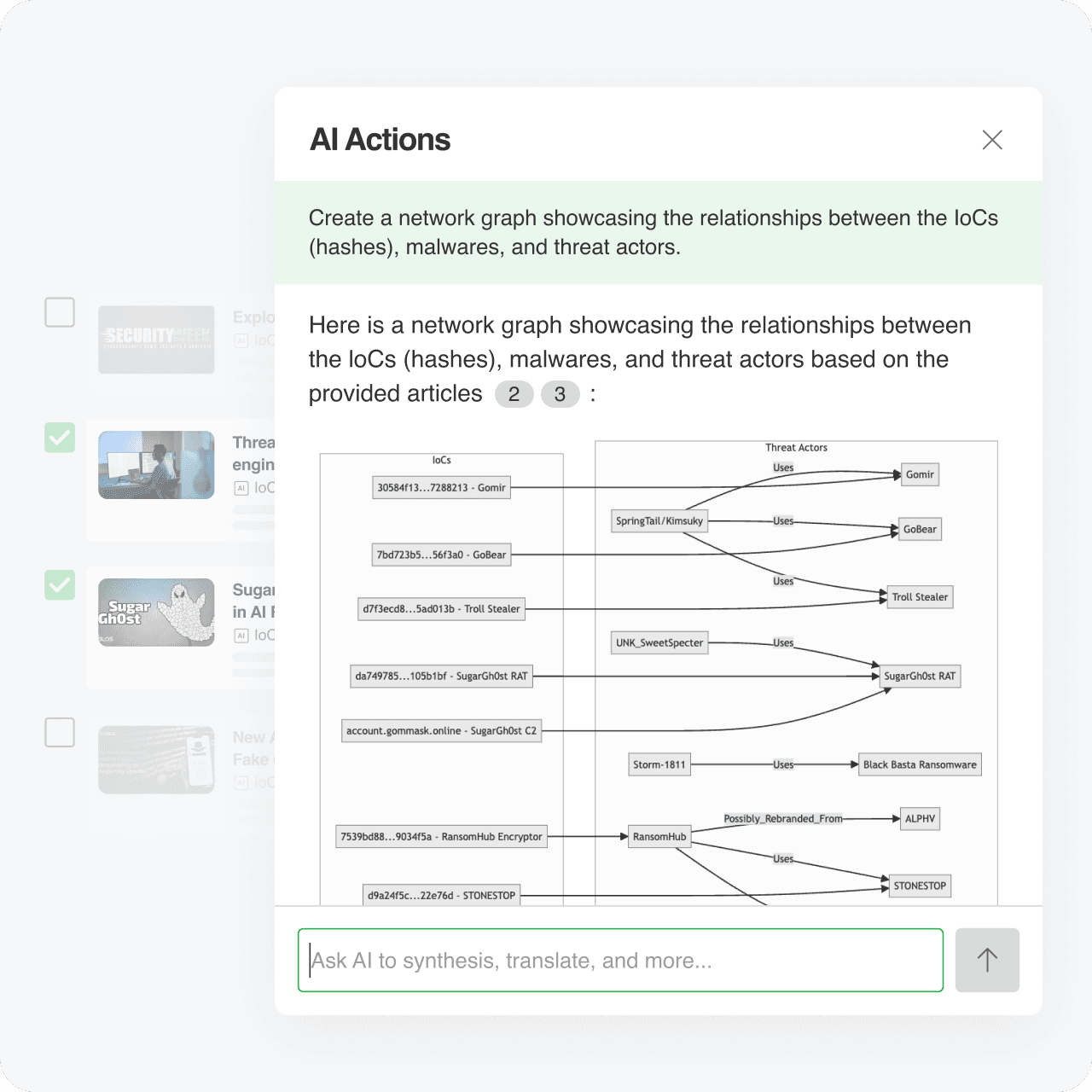
AI Actions
Extract specific indicators from multiple articles
Inspect threat reports for IoCs related to a particular threat actor or technique and copy into a report along with citations to sources

“Extracting IoCs from a single article used to take 45 minutes, now it’s automated.”
Per Kroghrud
CTI Team Lead, Sopra Steria Scandinavia
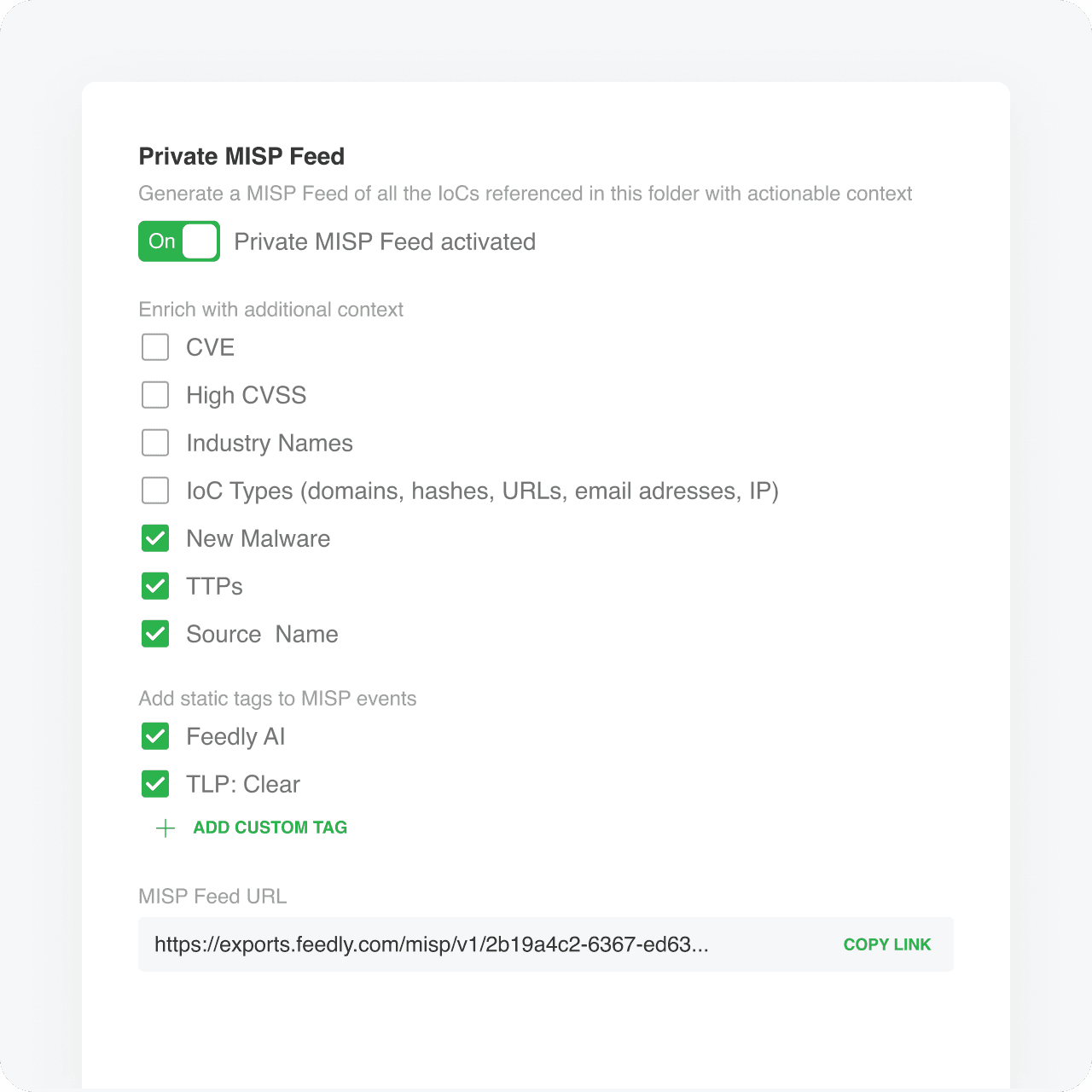
STIX & MISP Export
Ingest IoCs with rich contextual data into your MISP or SIEM
Accelerate your analysis with context like related threat actors, malware, vulnerabilities, TTPs, industries, etc.
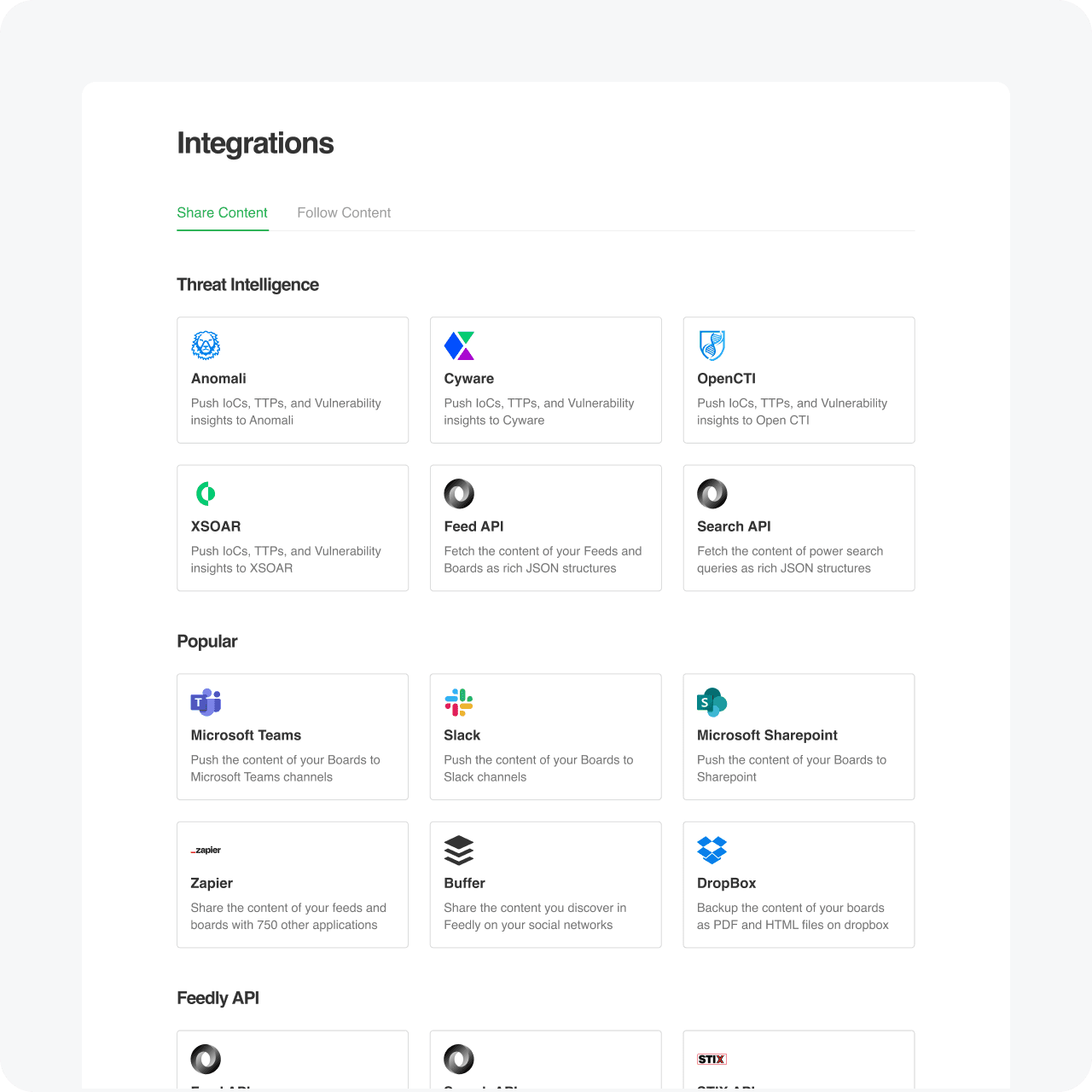
Integrations
Simple no-code integrations
Periodically ingest all the reports and artifacts collected into your MISP, SIEM, or other tool
Consolidate data into your tool of choice
Ingest IoCs from AI Feeds or curated Boards
Add static tags to trigger additional workflows
