Monitor threat actor behavior (TTPs)
Feedly AI extracts TTPs from the open web along with related context to accelerate your research
No credit card required
AI Feeds
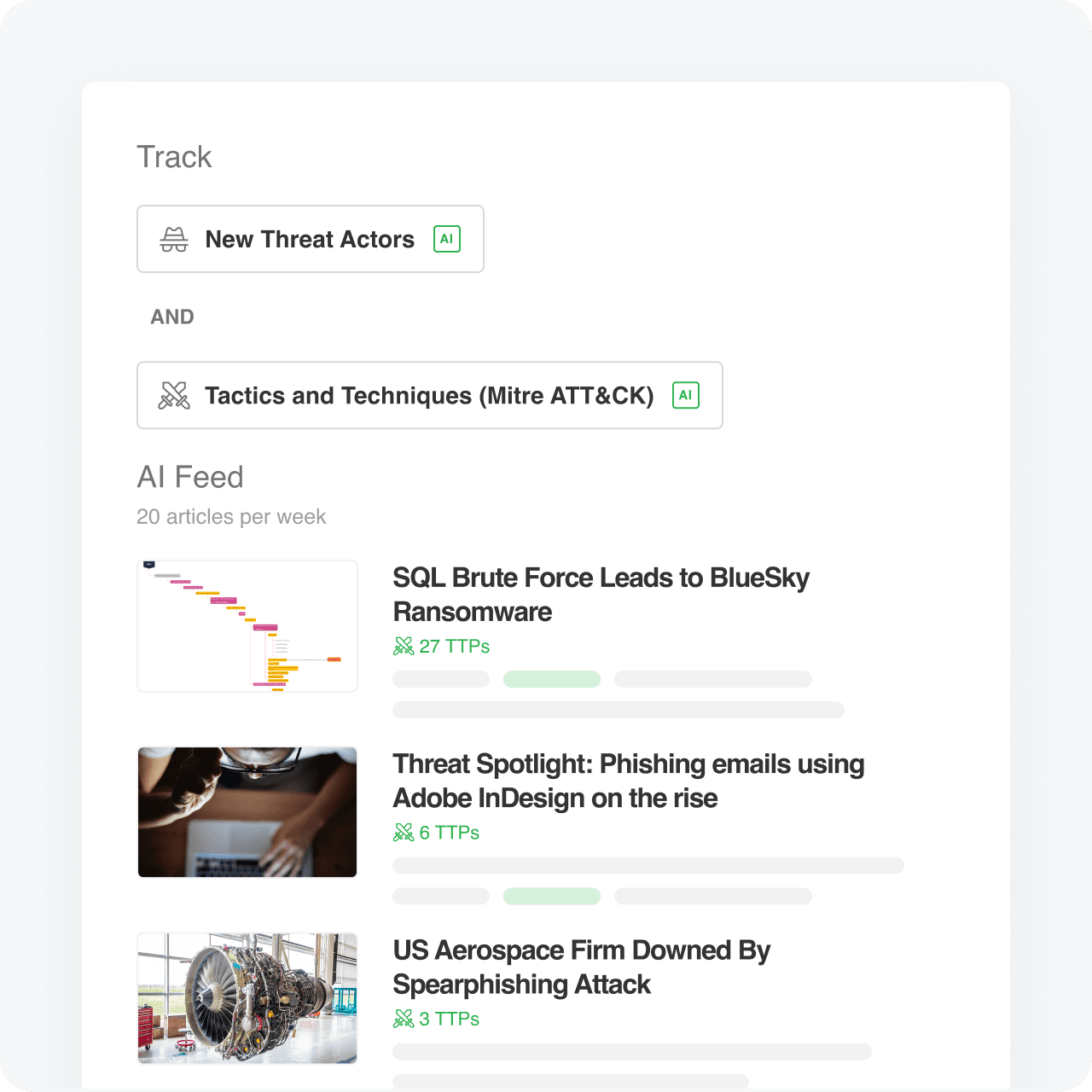
Collect threat intel reports and articles referencing TTPs
AI Feeds are AI-powered queries that collect actionable intelligence from the open web
Track threat actors targeting your industry
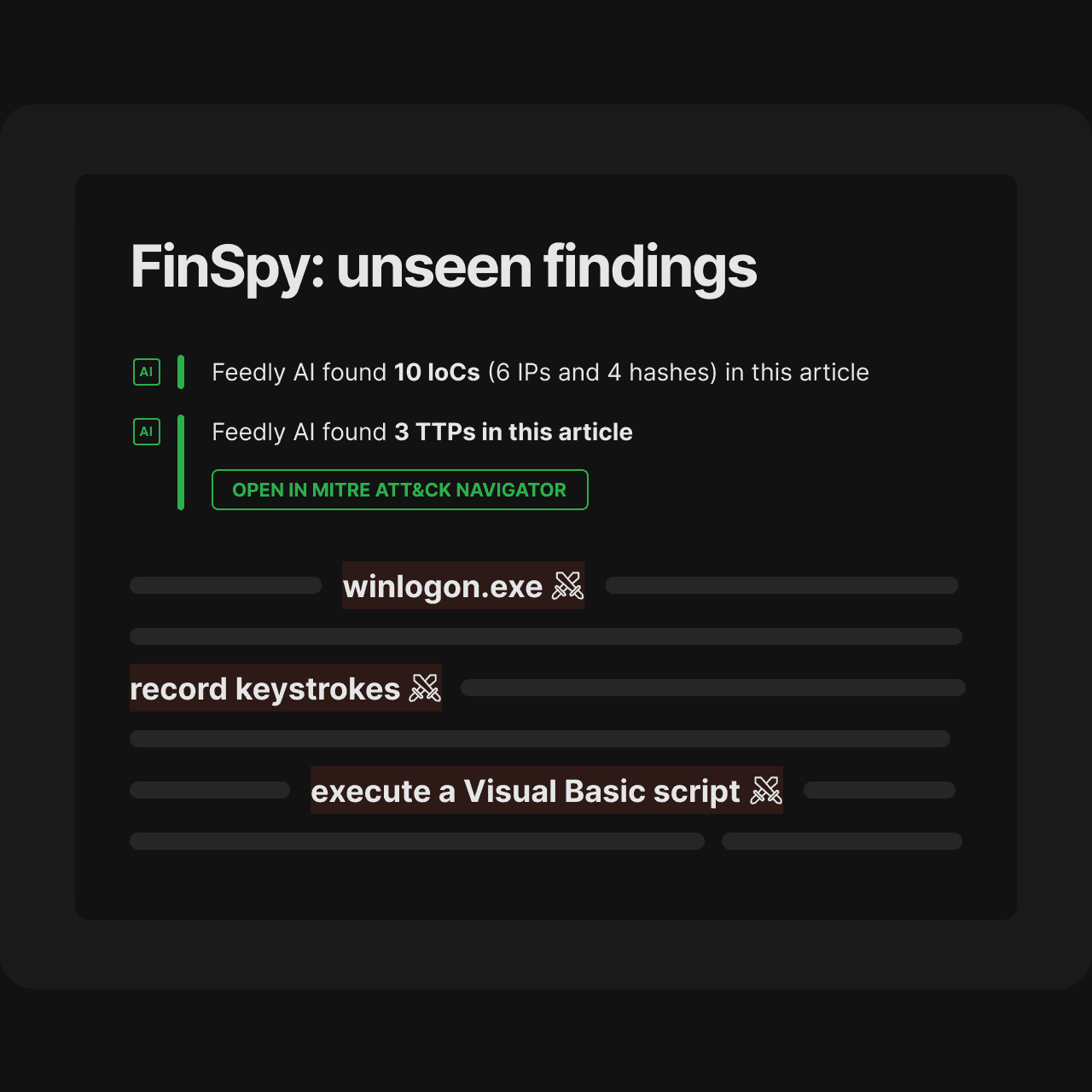
IoCs, malware, CVEs and related context
Continuously search 140M sources
AI Insights
Automatically extract TTPs and context
Feedly AI automatically tags TTPs hidden in phrases by understanding related context, not just ID numbers
Associate TTPs with threat actors
Malware, IoCs, and CVEs
Export in STIX 2.1 for use in other tools
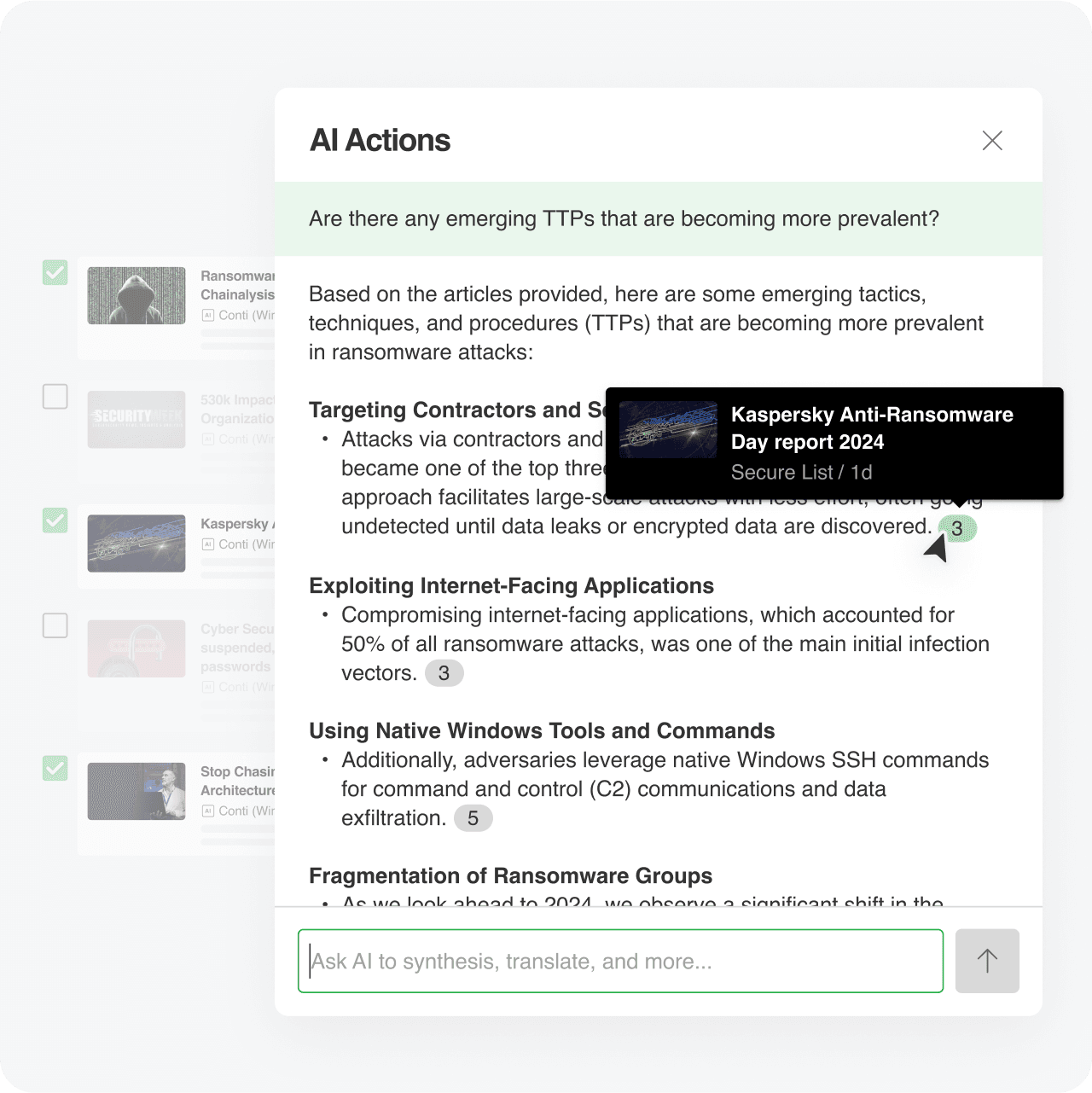
AI Actions
Collect TTPs associated with your adversaries
Inspect articles and extract TTPs associated with your targeted threat actors
Analyze trusted reports or advisories
Customize the output contents and format
Verifiable though source citations
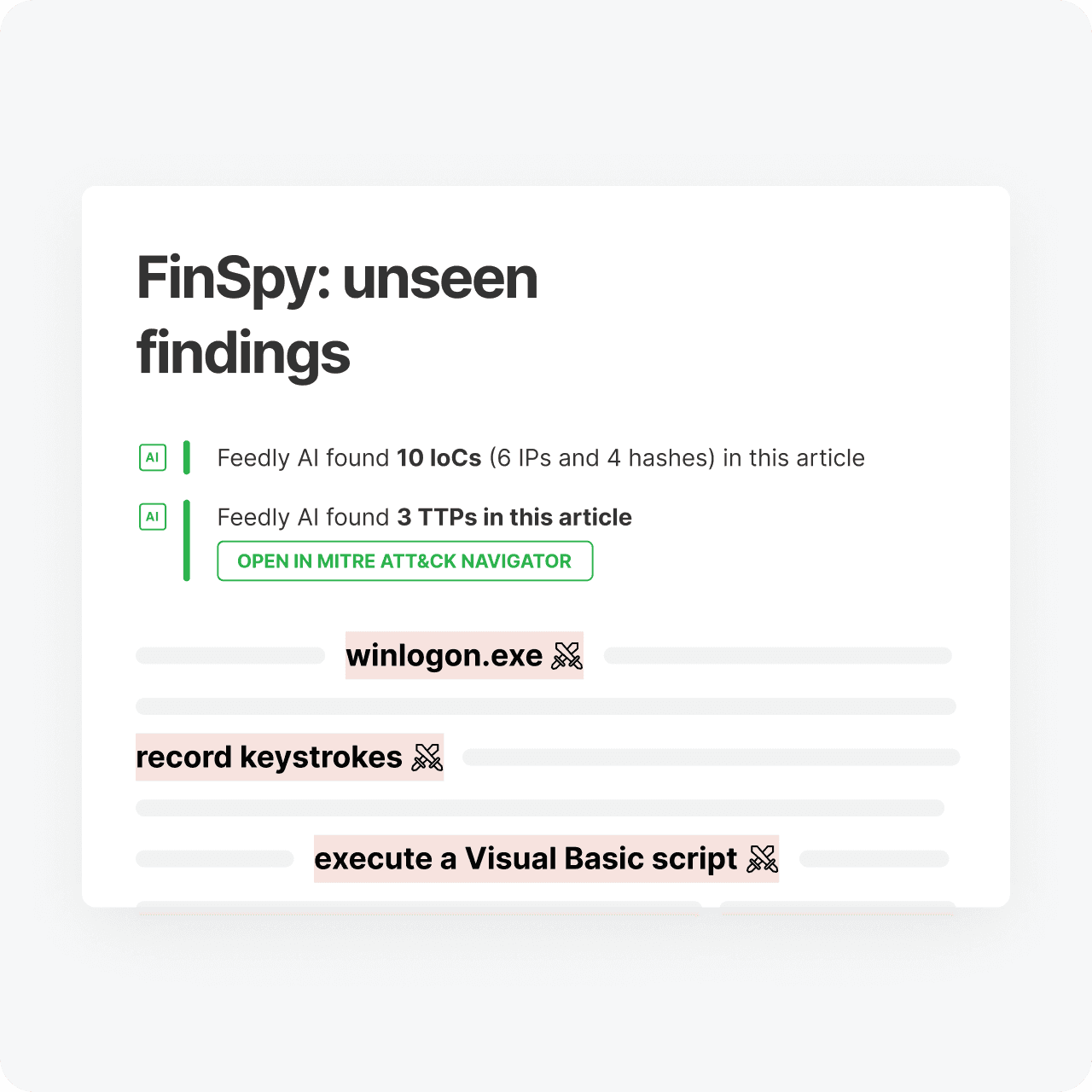
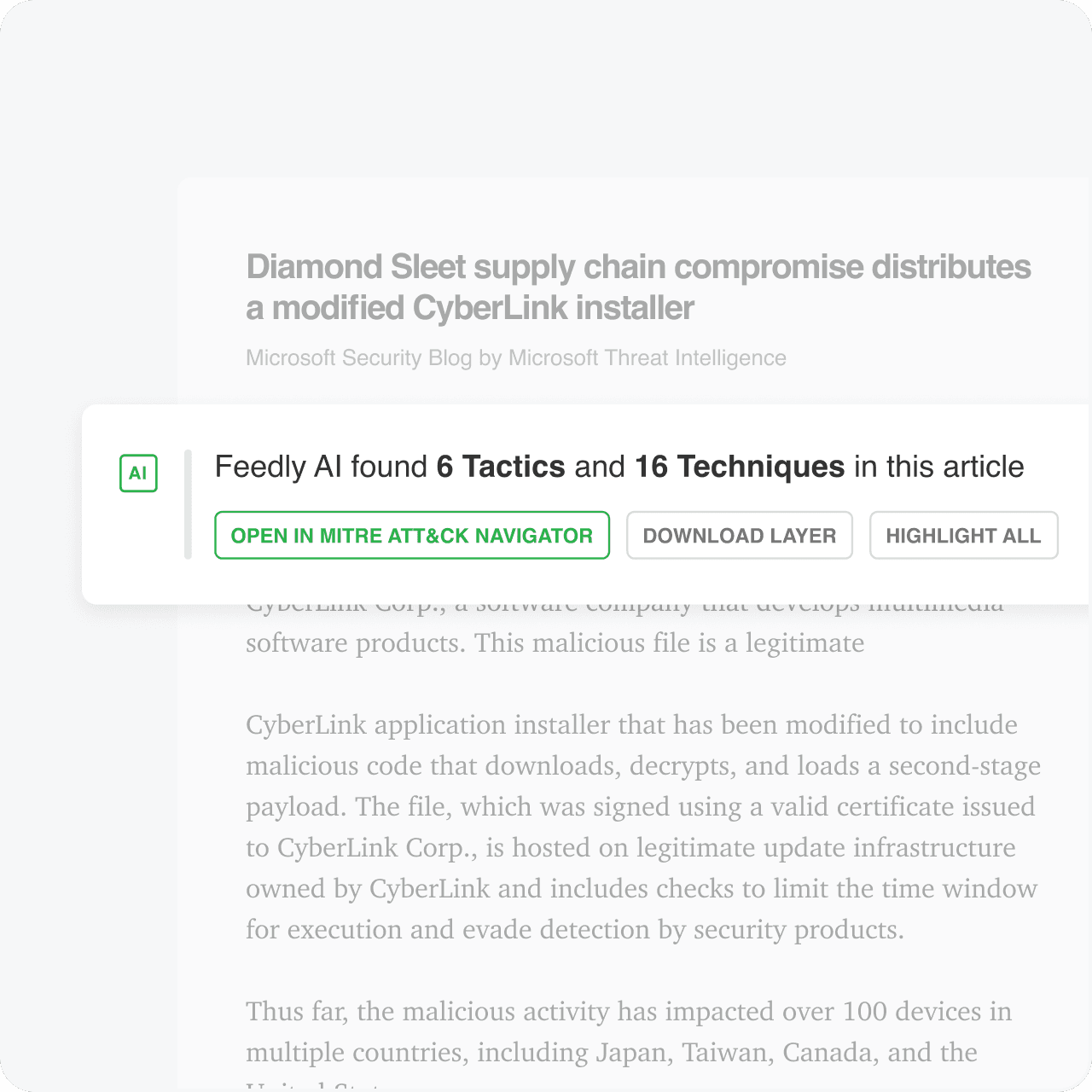
MITRE ATT&CK
Automate mapping TTPs to MITRE ATT&CK Navigator
Visualize TTPs in the ATT&CK Navigator to spot defensive gaps and mitigation opportunities
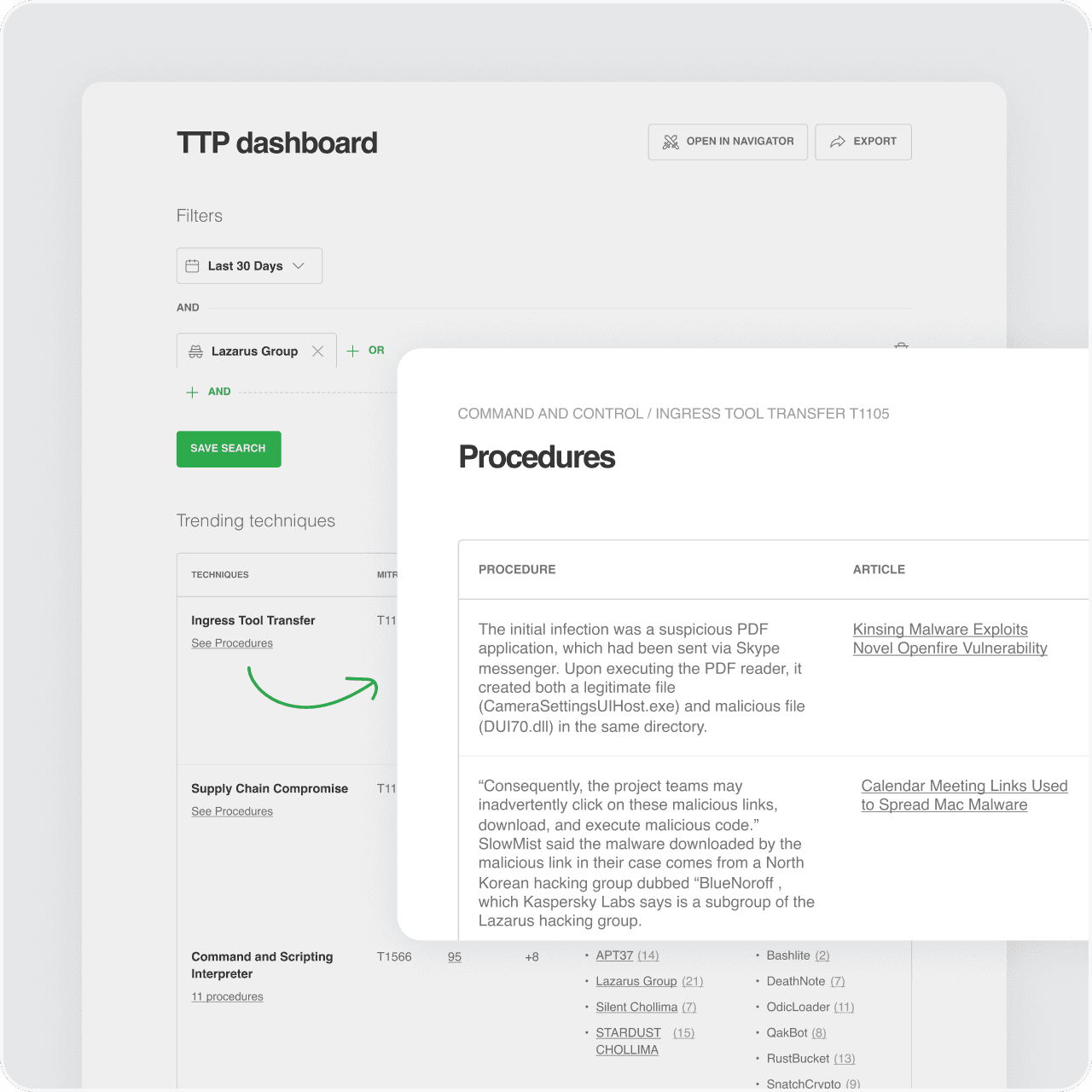
TTP Dashboard
Identify new threat actor behavior and procedures
Track trending techniques, dive into procedures, and view associated threat actors and malware
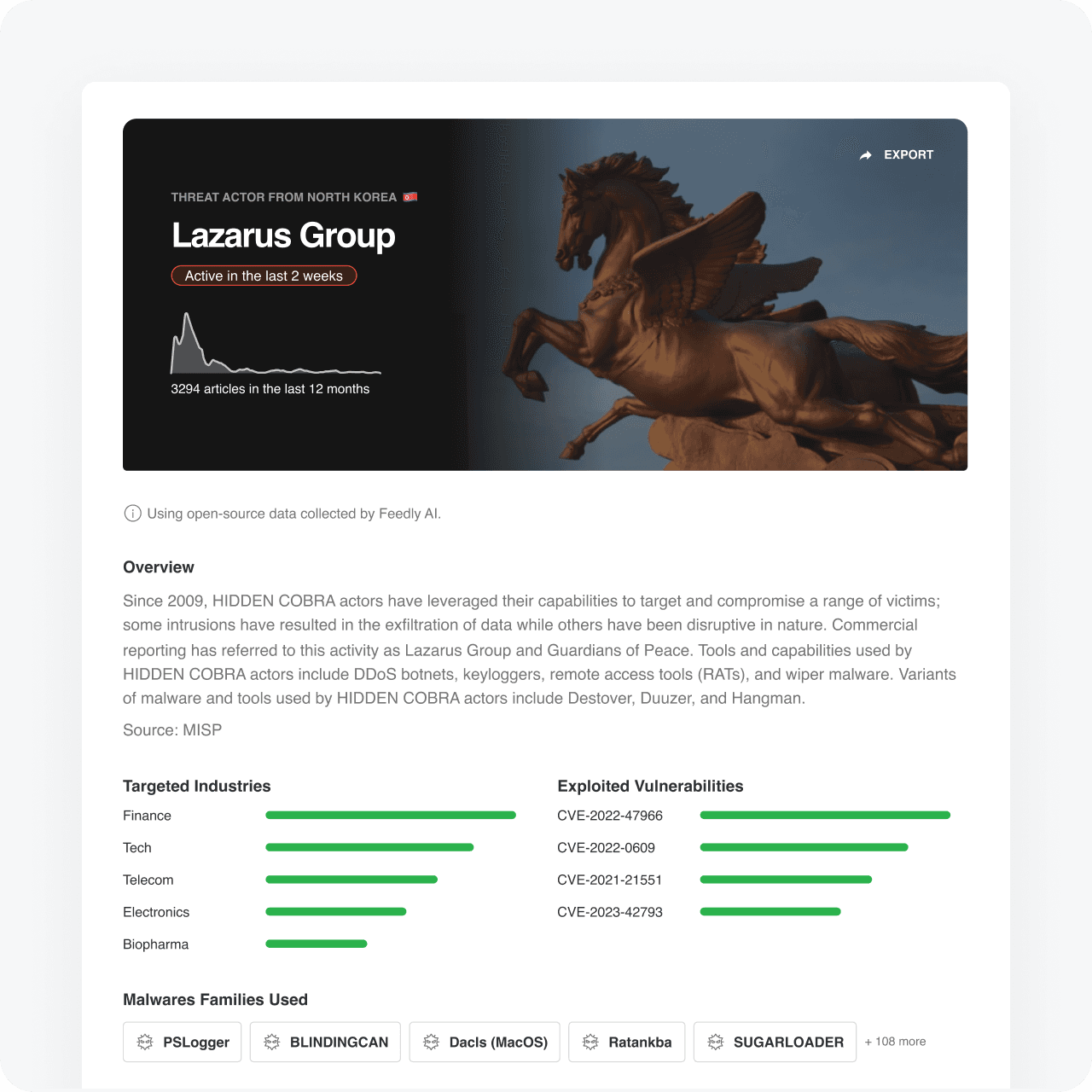
Threat Actor Insights Cards
Share actionable adversary insight with your team
Start your research with a 360 degree view of threat actors with the threat actor insights card
Targeted countries and industries
TTPs, malware, exploited vulnerabilities, and detection rules
Supports intel reports and the latest news

“You’d have to hire six full-time employees working full time to have the same 24/7 coverage of threat research that our automated process with Feedly currently handles.”
Edward Crispen
Lead DevOps Engineer, SecureCyber Defense
Explore more ways cyber security teams use Feedly to stay one step ahead
Get Started
Start discovering threat actor behavior in minutes
Get Started For Free
No credit card required
